0x00 前言
最近通过公安朋友了解到一起传销诈骗案件,涉及的项目叫“有钱还众筹骗局”。
玩法:按照官方的说法,我们注册有钱还这个APP之后,需要支付400元,然后享受众筹还债的权利。比如,你注册了之后,然后拉新三人,这三人每人缴纳400元,则每人可以替你还款200元,即600元。这不是传销么?

0x01 渗透流程简述
访问网站,注册了一个账号如下图:
对网站进行ip查询,服务器为香港阿里云服务器,whois也无可利用信息。
接着对网站目录扫描,发现admin.php文件后台,看到此后台可以看到有钱还管理系统,想法:通过关键词,关键特征搜索此源码,对源码进行代码审计。
紧接着百度搜索引擎搜索”有钱还源码”,
在网盘搜找到此套系统源码,对源码代码审计。

0x02 代码审计
将源码成功搭建后,对此源码进行分析,结果如下:
sql注入
\system\mod\index\index.mod.php
news_info函数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| public function news_info(){
if($this->post){
$n_id = $_POST['n_id'];
$news = $this->db->query('select * from w_class WHERE id='.$n_id, 2);
if(!empty($news)){
$news['n_img'] = $this->setup_img($news['n_img']);
$news['n_time'] = date('Y-m-d H:i',$news['n_time']);
echo json_encode(array(
'news'=>$news,
'code'=>200,
));
exit();
}else{
echo json_encode(array('code' => 404, 'msg' => '文章信息不存在'));
exit();
}
}
}
|
$n_id 参数传入未过滤,可操控sql查询,数字型盲注
payload:
1
2
3
4
| post
http:
n_id=123123123 and 1=2
|
\system\mod\index\plan.mod.php
plan_add函数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| public function plan_add()
{
if ($this->post) {
$fields = $this->SafeFilter($_POST);
$this->checkuser($fields);
$uid = $fields['uid'];
$cash = $this->db->query('select * from w_cash where `c_status`=1 AND c_uid='.$uid, 2);
if (!empty($cash)) {
echo json_encode(array('code' => 302, 'msg' => '众筹已激活,不能发起还款计划'));
exit();
}
if ($fields['j_price'] == false) {
echo json_encode(array('code' => 404, 'msg' => '债务金额无效'));
exit();
}
if (isset($_FILES['j_bor_img'])) {
$fields['j_bor_img'] = $this->uploads('j_bor_img');
}
if ($fields['j_bor_img'] == '') {
echo json_encode(array('code' => 404, 'msg' => '债务凭证不能为空'));
exit();
}
$jh = array(
'j_uid' => $uid,
'j_price' => $fields['j_price'],
'j_type' => $fields['j_type'],
'j_bor_img' => $fields['j_bor_img'],
'j_ctime' => time(),
'j_status' => 0,
);
$is_res = $this->db->insert('w_jihua', $jh);
if ($is_res) {
echo json_encode(array('code' => 200, 'msg' => '添加成功'));
exit();
} else {
echo json_encode(array('code' => 302, 'msg' => '添加失败'));
exit();
}
}
}
|
SafeFilter函数过滤sql注入,进入函数
addslashes保护给单引号(’)、双引号(”)、反斜线(\)与NUL(NULL字符)加上反斜线转义
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| public function SafeFilter($arr)
{
$ra = Array('/([\x00-\x08,\x0b-\x0c,\x0e-\x19])/', '/script/', '/javascript/', '/vbscript/', '/expression/', '/applet/', '/meta/', '/xml/', '/blink/', '/link/', '/style/', '/embed/', '/object/', '/frame/', '/layer/', '/title/', '/bgsound/', '/base/', '/onload/', '/onunload/', '/onchange/', '/onsubmit/', '/onreset/', '/onselect/', '/onblur/', '/onfocus/', '/onabort/', '/onkeydown/', '/onkeypress/', '/onkeyup/', '/onclick/', '/ondblclick/', '/onmousedown/', '/onmousemove/', '/onmouseout/', '/onmouseover/', '/onmouseup/', '/onunload/');
if (is_array($arr)) {
foreach ($arr as $key => $value) {
if (!is_array($value)) {
if (!get_magic_quotes_gpc()) {
$value = addslashes($value);
}
$value = preg_replace($ra, '', $value);
$arr[$key] = $value;
} else {
$this->SafeFilter($arr[$key]);
}
}
}
return $arr;
}
|
uid参数传入为数字型,sql拼接,无需单双引号跳出,存在uid数字型注入
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| POST /index.php?m=plan&c=plan_add HTTP/1.1
Host: www.xxx.cn
Content-Length: 3899
Accept: *
|
储存型xss
前台审核储存型xss绕过
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| public function real_name(){
if($this->post){
$fields = $this->SafeFilter($_POST);
$user = $this->checkuser($fields);
$uid = $fields['uid'];
if($fields['m_zsxm'] == ''){echo json_encode(array('code' => 404, 'msg' => '真实姓名不能为空'));exit();}
if($fields['m_carid'] == ''){echo json_encode(array('code' => 404, 'msg' => '身份证号不能为空'));exit();}
if(isset($_FILES['m_carimg1'])){
$fields['m_carimg1'] = $this->uploads('m_carimg1');
}
if($fields['m_carimg1'] == ''){echo json_encode(array('code' => 404, 'msg' => '请上传身份照片'));exit();}
if(isset($_FILES['m_carimg2'])){
$fields['m_carimg2'] = $this->uploads('m_carimg2');
}
if($fields['m_carimg2'] == ''){echo json_encode(array('code' => 404, 'msg' => '请上传身份照片'));exit();}
$set_sm = array(
'm_zsxm' => $fields['m_zsxm'],
'm_carid' => $fields['m_carid'],
'm_carimg' => $fields['m_carimg1'].','.$fields['m_carimg2'],
);
$is_res = $this->db->update('w_users',$set_sm,array('id'=>$uid));
if($is_res){
$this->SetupUser($uid,$fields['m_zsxm']);
echo json_encode(array('code' => 200, 'msg' => '上传成功,等待审核'));exit();
}else{
echo json_encode(array('code' => 302, 'msg' => '上传失败'));exit();
}
}
}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| public function SafeFilter($arr)
{
$ra = Array('/([\x00-\x08,\x0b-\x0c,\x0e-\x19])/', '/script/', '/javascript/', '/vbscript/', '/expression/', '/applet/', '/meta/', '/xml/', '/blink/', '/link/', '/style/', '/embed/', '/object/', '/frame/', '/layer/', '/title/', '/bgsound/', '/base/', '/onload/', '/onunload/', '/onchange/', '/onsubmit/', '/onreset/', '/onselect/', '/onblur/', '/onfocus/', '/onabort/', '/onkeydown/', '/onkeypress/', '/onkeyup/', '/onclick/', '/ondblclick/', '/onmousedown/', '/onmousemove/', '/onmouseout/', '/onmouseover/', '/onmouseup/', '/onunload/');
if (is_array($arr)) {
foreach ($arr as $key => $value) {
if (!is_array($value)) {
if (!get_magic_quotes_gpc()) {
$value = addslashes($value);
}
$value = preg_replace($ra, '', $value);
$arr[$key] = $value;
} else {
$this->SafeFilter($arr[$key]);
}
}
}
return $arr;
}
|
SafeFilter函数过滤xss,可以看到是字符传入判断,这个大小写绕过就行
因参数过滤不足,在前台身份证认证存在xss漏洞,大小写绕过插入数据库,后台无实体化过滤,从而产生储存型xss
rce 前后台任意文件上传getshell
\system\mod\admin\config.mod.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| public function upload(){
if($_FILES["file"]["error"]){
echo json_encode(array('code'=>1,'msg'=>'发生错误'));exit();
}else{
if(($_FILES["file"]["type"]=="image/png"||$_FILES["file"]["type"]=="image/jpeg")&&$_FILES["file"]["size"]<1024000){
$filename =substr(strrchr($_FILES["file"]["name"], '.'), 1);
$filename ="./static/upload/".date('Ymd',time()).$this->getMillisecond().'.'.$filename;
if(file_exists($filename)){
echo json_encode(array('code'=>1,'msg'=>'刷新后重试'));exit();
}else{
move_uploaded_file($_FILES["file"]["tmp_name"],$filename);
echo json_encode(array('code'=>0,'msg'=>$filename));exit();
}
}else {
echo json_encode(array('code'=>1,'msg'=>'类型不允许'));exit();
}
}
}
|
文件未做身份限制,文件名未做后缀限制,可任意访问,上传文件。
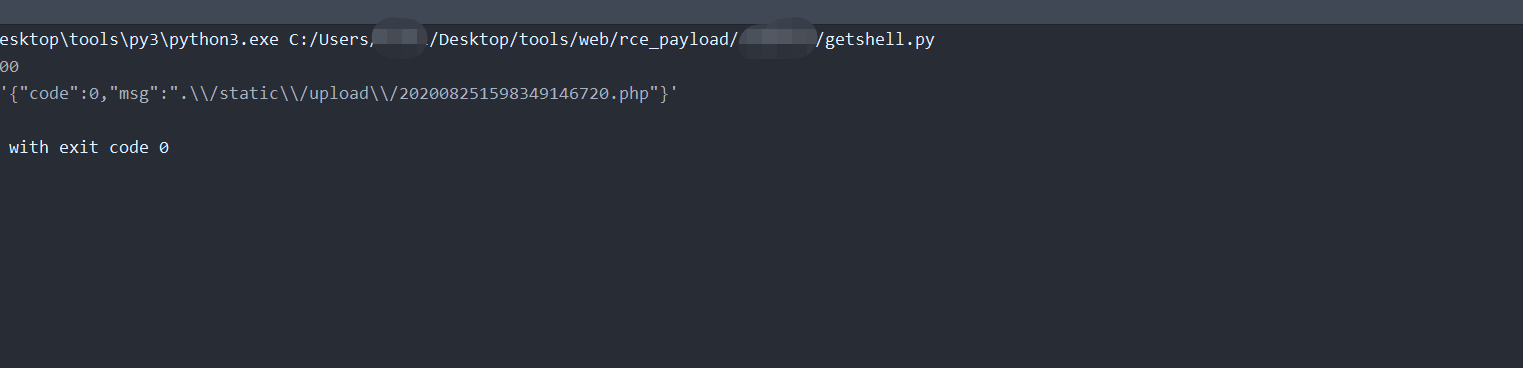
0x04 后续
通过上述审计出的漏洞,获取到服务器权限,并且通过xss落地该团伙位置
1
2
| 落地时间,网站地址,域名,落地ip,端口,落地
2020-05-24 17:12:37,http://xxx.com/admin.php,xxx.com,112.1.2.1,57217,中国 江苏 苏州
|
该犯罪团伙订单数6万余条
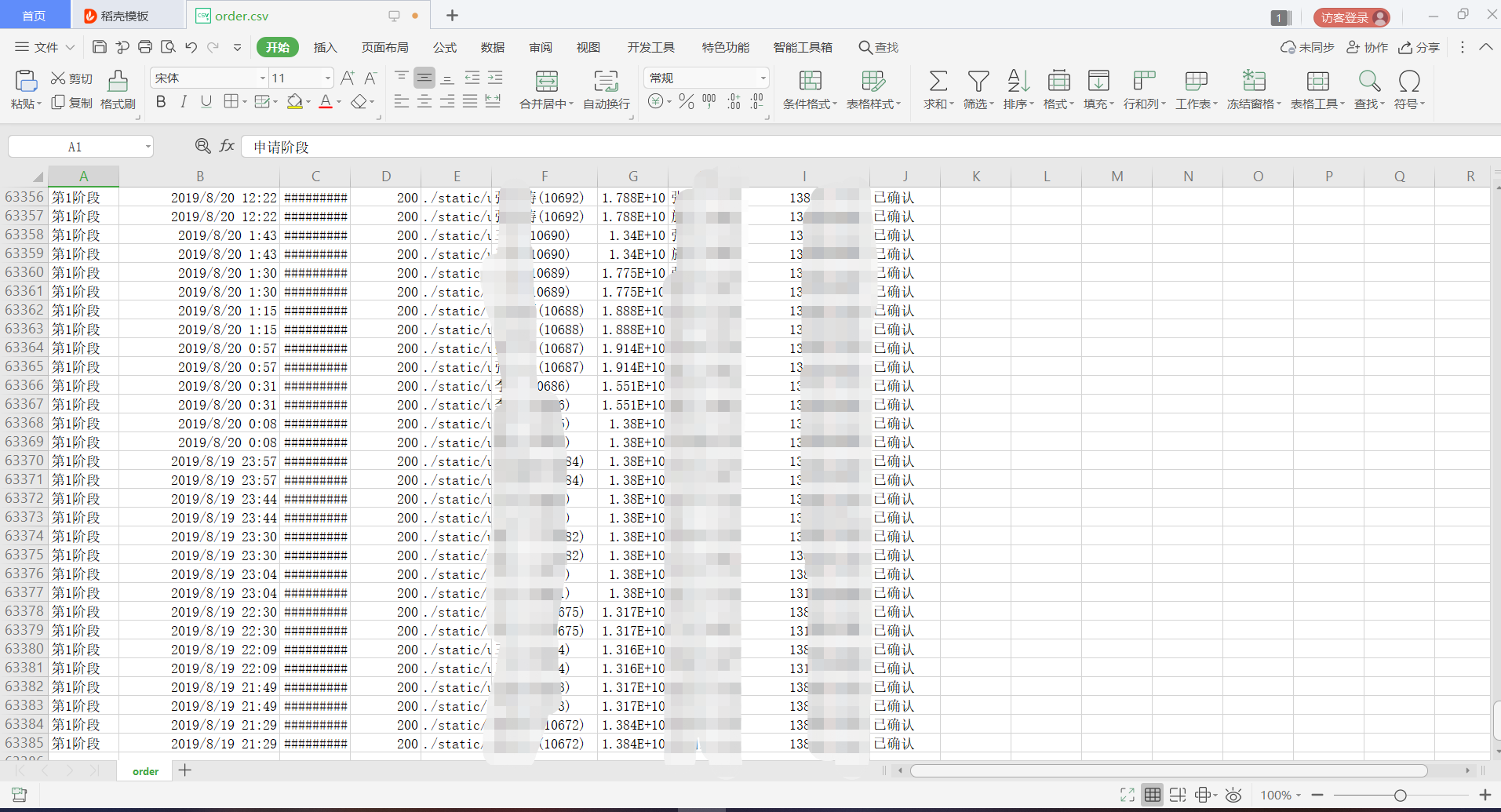
传销2万多用户
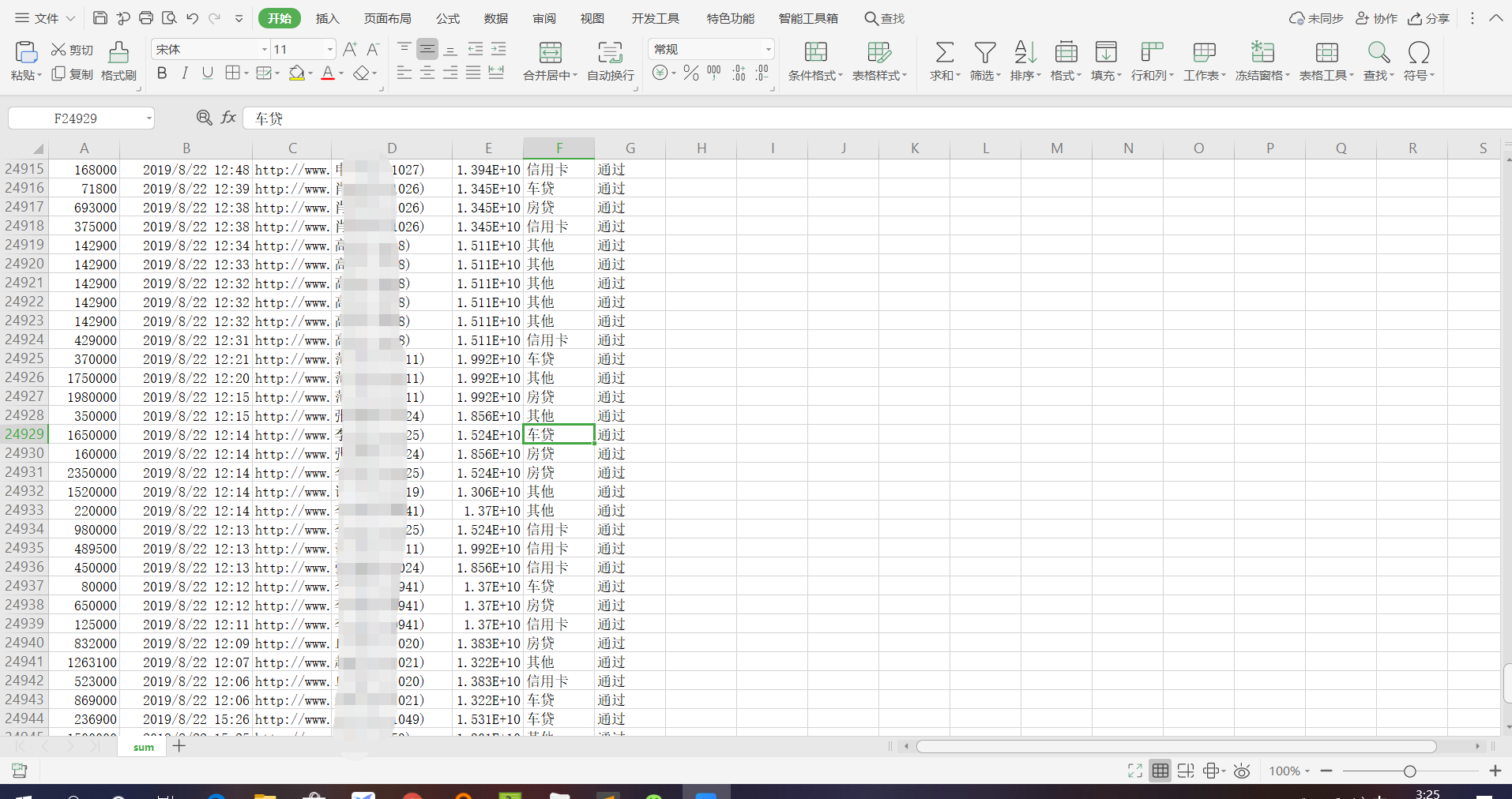
难以想象的是,如此拙劣的骗术,为什么还会有这么多人受骗?跟朋友py交易完就开溜,莫贪心。
谢谢观看!
0x05 总结
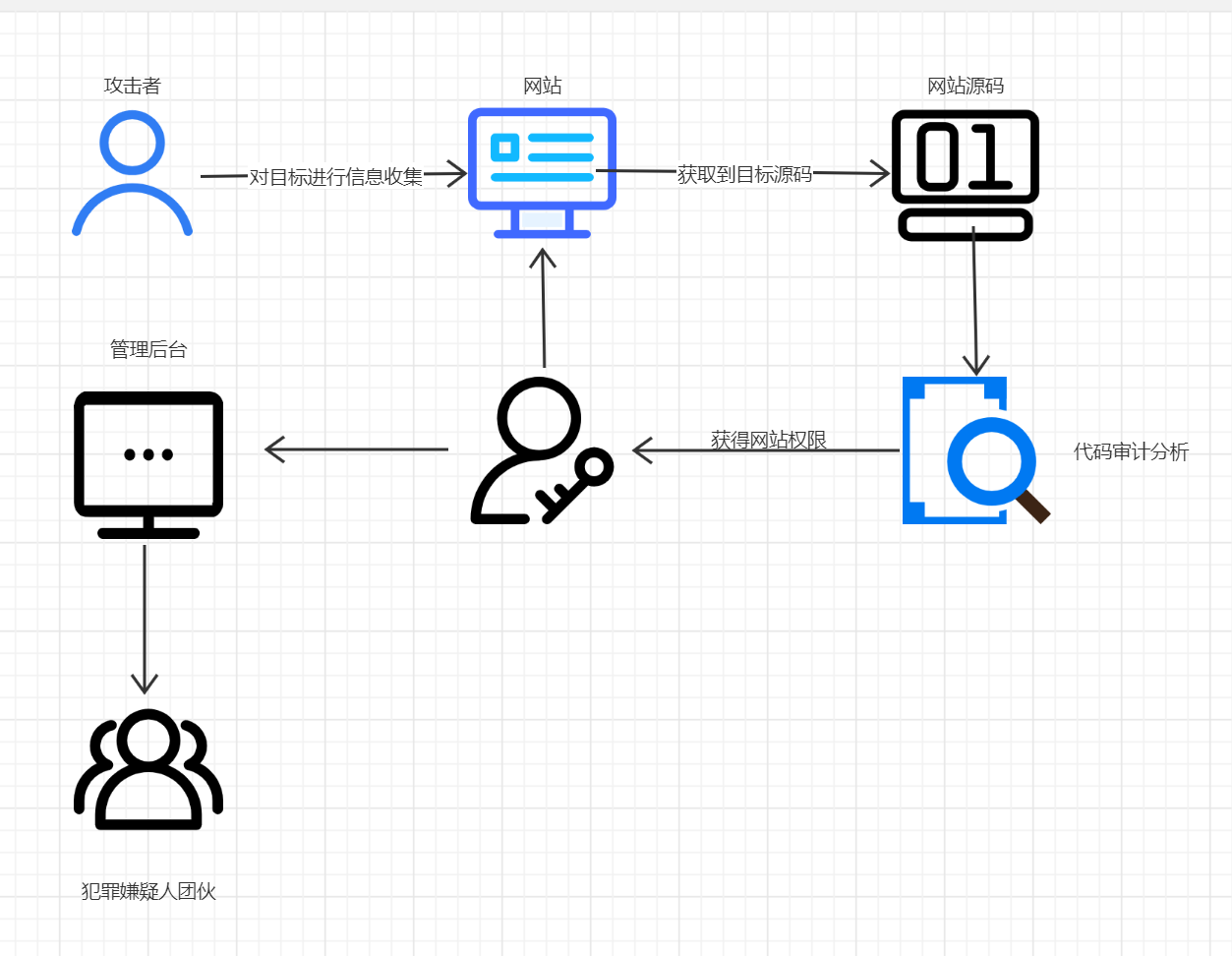
1、渗透测试总获取到网站源码是很关键因素,获取到源码相当于摸清网站所有得结构
2、信息收集对渗透测试得重要性,获取到目标越多信息,对渗透测试越有利











